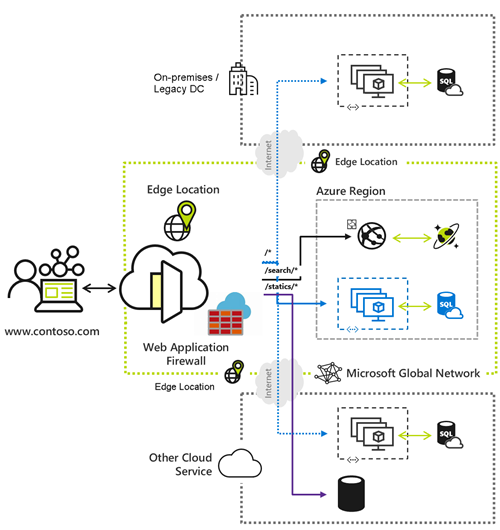
To set up Web Application Firewall (WAF) rules in Azure Front Door, you can follow these steps, which involve creating a WAF policy and configuring it with either managed rules or custom rules. This process can be done through the Azure portal.

Creating a WAF Policy
- Start the Creation Process: In the Azure portal, select “Create a resource”. Search for “WAF”, select “Web Application Firewall (WAF)”, and then click “Create” [1].
- Configure Basic Settings: On the “Basics” tab of the “Create a WAF policy” page, you need to specify:
- Policy for: Select “Global WAF (Front Door)”.
- Front door tier: Choose between “Classic”, “Standard”, and “Premium” tiers.
- Subscription: Select your Azure subscription.
- Resource group: Choose your Azure Front Door resource group name.
- Policy name: Enter a unique name for your WAF policy.
- Policy state: Set as “Enabled” [1].
Configuring WAF Rules
After creating the WAF policy, you can configure it with either managed rules or custom rules.
Managed Rules
- Default Rule Set: Azure Front Door comes with a managed Default Rule Set (DRS) that is enabled by default for the Premium and Classic tiers. The current DRS for the Premium tier is
Microsoft_DefaultRuleSet_2.0, and for the Classic tier, it’sMicrosoft_DefaultRuleSet_1.1. You can assign a different DRS or disable individual rules as needed [1]. - Managed Rules Support: Managed rules are only supported in the Azure Front Door Premium and Classic tier policies. They provide an easy way to deploy protection against a common set of security threats, with rules updated by Azure to protect against new attack signatures [2].
Custom Rules
- Custom Rule Types: Azure Front Door allows you to create custom WAF rules that control access based on conditions you define. Custom rules can be match rules, which control access based on matching conditions, or rate limit rules, which control access based on matching conditions and the rates of incoming requests [2].
- Example Custom Rule: Here’s an example of a custom rule that blocks requests where the URL is longer than 100 characters:
{
"name": "URLOver100",
"priority": 5,
"ruleType": "MatchRule",
"matchConditions": [
{
"matchVariable": "RequestUri",
"selector": null,
"operator": "GreaterThanOrEqual",
"negateCondition": false,
"matchValue": [
"100"
]
}
],
"action": "Block"
}This rule checks if the request URI is greater than or equal to 100 characters and blocks the request if the condition is met [3].
WAF Policy and Rules
- Policy and Rules Association: A WAF policy can be associated with one or more Azure Front Door domains for protection. The policy consists of custom rules created by the customer and managed rule sets, which are collections of Azure-managed preconfigured sets of rules. Custom rules are processed before managed rule sets [4].
- WAF Policy States and Modes: A WAF policy can be enabled or disabled. When enabled, WAF actively inspects incoming requests and takes actions according to rule definitions. You can also configure the WAF policy to run in detection mode (monitoring and logging requests) or prevention mode (taking specified actions if a request matches a rule) [5].
By following these steps, you can effectively set up WAF rules in Azure Front Door to protect your web applications from common vulnerabilities and exploits.
References:
[1] https://learn.microsoft.com/en-us/azure/web-application-firewall/afds/waf-front-door-create-portal
[2] https://learn.microsoft.com/en-us/azure/frontdoor/web-application-firewall
[3] https://learn.microsoft.com/en-us/azure/web-application-firewall/afds/waf-front-door-custom-rules
[4] https://learn.microsoft.com/en-us/azure/web-application-firewall/afds/afds-overview
[5] https://learn.microsoft.com/en-us/azure/web-application-firewall/afds/waf-front-door-policy-settings